Summary of the DSAR Process
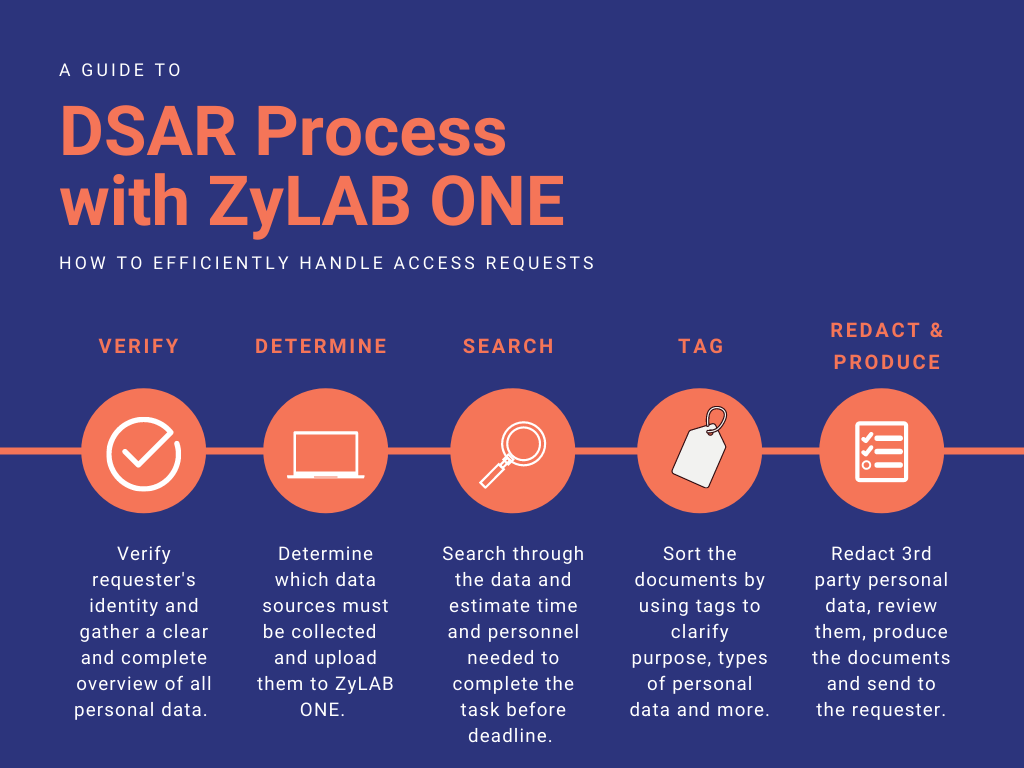
After receiving an access request, the first important step is to verify the identity of the requester. This is of paramount importance, as it would result in a data breach to provide personal data to an unauthorized person.
The second step is to determine the necessary data sources to be searched for responding to the DSAR. Make a list of all possible data sources that are needed and the names of the people who might have been involved, such as managers, HR staff, clients etc. It is also important to make a list of potential recipients of the data as data subjects have the right to know this information.
After determining the data sources and recipients, proceed to determine the time frame of the search to narrow down the search and the amount of data that need to be searched.
Before the actual search, it is advisable to produce a report from the documents following a quick search of i.e. requester’s names, and to estimate the time and personnel needed to respond to the DSAR within one month – and whether or not it is necessary to extend the deadline due to complexity of the request.
Once you have established how much time you need, you may proceed to search through the dataset and find relevant documents and tag them for a better overview. Searching through the dataset is the foundation of handling an access request. By using efficient search techniques and queries, all relevant documents can be found and filtered by using tags.
According to the GDPR, controllers must clarify the purposes of processing and the recipients of the personal data when they are responding to a subject access request. By using the 04 Purpose and Recipients tag, you can easily clarify the purposes of processing and whether or not there are any recipients with whom the requester’s personal data has been shared.
The documents may be tagged to clarify the purposes of processing, to determine whether or not the documents need to be redacted, and to specify which type of personal data are being processed.
After the tagging process has been completed, proceed to redact documents with the redaction tag and review them for reassurance. The documents are then ready to be produced and sent to the requester.